Okay, let's be real for a second "“ if you're reading this, your computer is probably acting sus AF, or you're just being smart about cybersecurity (which honestly, respect 💯).
Whether your PC is running slower than your WiFi during peak hours, getting random pop-ups that are more annoying than TikTok ads, or you suspect some sketchy malware is living rent-free on your system, you've come to the right place.
We're about to dive deep into the best malware removal tools that'll help you reclaim your digital space and keep your Windows computer running smoother than your favorite playlist.
What Is Malware and Why Should You Care?
Malware, short for malicious software, is basically any program designed to harm, disrupt, or gain unauthorized access to your computer. Think of it as digital parasites that nobody invited to the party. These cyber threats come in various forms, each more annoying than the last.
Types of Malware Threatening Your Windows PC
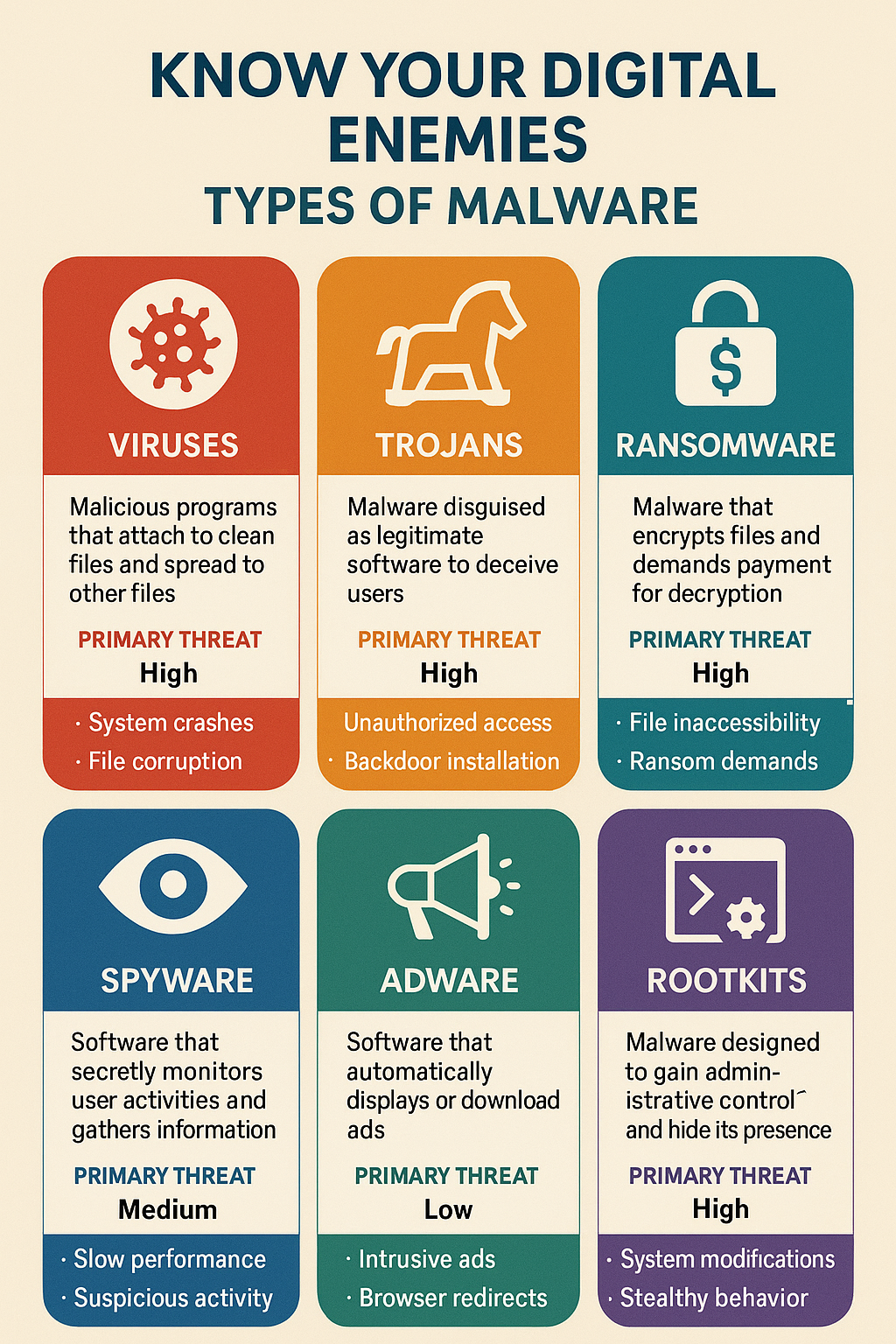
Viruses are the classic troublemakers that replicate themselves and spread to other files and computers. They're like that one friend who overstays their welcome and brings uninvited guests.
Trojans disguise themselves as legitimate software but contain malicious code. They're the ultimate catfish of the cyber world "“ looking innocent but hiding dangerous intentions.
Ransomware is perhaps the most terrifying type, encrypting your files and demanding payment for their release. It's essentially digital kidnapping of your precious data.
Spyware secretly monitors your activities, stealing sensitive information like passwords, credit card numbers, and browsing habits. It's like having an invisible stalker tracking your every move online.
Adware bombards you with unwanted advertisements and pop-ups, making your browsing experience more frustrating than trying to skip YouTube ads.
Rootkits hide deep within your system, giving hackers backdoor access to your computer while remaining virtually undetectable.
Signs Your Windows Computer Has Malware
Recognizing malware infection early can save you from serious damage. Here are the telltale signs that something's wrong:
Your computer suddenly becomes slower than usual, taking forever to boot up or open programs. Random pop-ups appear even when you're not browsing the web. Your web browser redirects you to suspicious websites you never intended to visit. Unknown programs appear in your startup list or running processes.
You notice unusual network activity or your internet data usage spikes unexpectedly. Files disappear, become corrupted, or get encrypted without your knowledge. Your antivirus software gets disabled mysteriously, or you can't access security websites.
Strange toolbars or extensions appear in your browser without installation. Your computer crashes frequently or displays the dreaded blue screen of death. You receive warnings about virus infections that seem fake or overly dramatic.
The Best Free Malware Removal Tools for Windows
1. Malwarebytes Anti-Malware
Malwarebytes stands as one of the most trusted names in malware detection and removal. The free version offers excellent on-demand scanning capabilities, effectively detecting and removing malware that traditional antivirus software might miss.
Key Features:
- Advanced malware detection using behavioral analysis
- Real-time protection against malicious websites
- Rootkit scanning and removal capabilities
- Quarantine system for safe malware handling
- Regular database updates for latest threat protection
Pros: Excellent detection rates, user-friendly interface, effective against zero-day threats, minimal system impact during scans.
Cons: Free version lacks real-time protection, limited customer support, some advanced features require premium subscription.
The software excels at detecting potentially unwanted programs (PUPs) and adware that other security solutions often overlook. Its signature-less detection technology identifies malware based on behavior rather than known signatures, making it highly effective against new and emerging threats.
2. Windows Defender (Microsoft Defender)
Windows Defender comes built into Windows 10 and 11, providing baseline protection without additional software installation. Microsoft has significantly improved its capabilities over recent years, making it a viable option for basic malware protection.
Key Features:
- Real-time protection against viruses and malware
- Cloud-based protection with machine learning
- Firewall and network protection
- Browser protection against malicious websites
- Parental controls and family safety features
Pros: Completely free, built into Windows, regular automatic updates, minimal system resource usage, integration with Windows Security Center.
Cons: Limited advanced features, fewer configuration options, may not catch all sophisticated threats, basic reporting capabilities.
Windows Defender performs well in independent lab tests and provides adequate protection for average users. However, it may struggle with advanced persistent threats and targeted attacks that require more sophisticated detection methods.
3. Avira Free Antivirus
Avira offers robust malware protection through its free antivirus solution, combining traditional signature-based detection with cloud intelligence for comprehensive threat protection.
Key Features:
- Real-time scanning and protection
- Browser safety extension
- Email protection scanner
- USB/removable media scanning
- Quarantine and repair functions
Pros: Excellent malware detection rates, lightweight system impact, user-friendly interface, free browser protection, regular updates.
Cons: Limited customer support for free users, advertisements for premium features, fewer advanced customization options.
Avira's cloud-based approach ensures quick updates for new threats while maintaining minimal impact on system performance. The software consistently ranks high in independent antivirus testing for both detection rates and usability.
4. AVG AntiVirus Free
AVG provides comprehensive malware protection through its free antivirus solution, offering real-time scanning and threat detection for Windows computers.
Key Features:
- Real-time protection against malware
- Email and web protection
- File scanning and quarantine
- Automatic security updates
- Basic firewall protection
Pros: Strong malware detection capabilities, intuitive user interface, minimal system slowdown, reliable real-time protection.
Cons: Limited advanced features in free version, occasional false positives, advertisements for premium upgrade.
AVG's strength lies in its balance between protection effectiveness and system performance. The software provides solid baseline security without overwhelming users with complex configuration options.
5. Bitdefender Antivirus Free Edition
Bitdefender's free offering provides powerful malware detection using the same core engine as their premium products, delivering enterprise-level protection without cost.
Key Features:
- Award-winning malware detection technology
- Real-time threat protection
- Minimal system resource usage
- Simple, unobtrusive interface
- Automatic security updates
Pros: Excellent detection rates, extremely lightweight, minimal false positives, simple setup and operation.
Cons: Very basic feature set, no customer support, limited configuration options, no additional security tools.
Bitdefender Free focuses purely on malware detection and removal, eschewing additional features for maximum effectiveness in its core function. This approach results in outstanding protection with virtually no system impact.

Premium Malware Removal Solutions
1. Norton 360 Deluxe
Norton 360 represents comprehensive cybersecurity protection, combining advanced malware detection with identity theft protection, VPN services, and cloud backup storage.
Key Features:
- Multi-layered malware protection
- Identity theft monitoring and alerts
- Secure VPN with unlimited data
- Cloud backup storage (50GB-500GB depending on plan)
- Password manager with secure vault
- Parental controls and time management
- Dark web monitoring for personal information
Advanced Protection Capabilities: Norton's SONAR behavioral protection technology monitors applications for suspicious activities, detecting previously unknown malware through behavioral analysis. The software includes advanced firewall protection with intrusion prevention, blocking unauthorized network access attempts.
Performance Impact: Despite its comprehensive feature set, Norton 360 maintains relatively low system impact through optimized scanning algorithms and intelligent resource management. Background scans run during idle periods to minimize performance disruption.
Pricing: Plans start around $49.99 annually for single device protection, with family plans covering up to 10 devices for approximately $99.99 per year.
2. Kaspersky Total Security
Kaspersky consistently ranks among the top antivirus solutions in independent testing, offering superior malware detection with advanced threat intelligence capabilities.
Key Features:
- Advanced malware detection and removal
- Real-time protection against cyber threats
- Secure payment protection for online transactions
- Password manager with secure storage
- File encryption and secure deletion
- Parental controls with content filtering
- VPN service with limited data allowance
Advanced Security Technologies: Kaspersky employs machine learning algorithms and behavioral analysis to identify unknown threats. The software includes application control features, preventing unauthorized software installation and execution.
System Performance: Kaspersky optimizes system performance through intelligent scanning schedules and resource management, ensuring minimal impact on daily computer usage.
Pricing: Individual licenses start around $59.99 annually, with multi-device family plans available for approximately $89.99 per year.
3. McAfee Total Protection
McAfee offers comprehensive security solutions with strong malware protection and additional privacy features for complete digital security.
Key Features:
- Real-time malware scanning and removal
- Web protection against malicious websites
- Email security and spam filtering
- Identity theft protection services
- Secure VPN for private browsing
- Password manager with autofill
- File shredder for secure deletion
Unique Security Features: McAfee's WebAdvisor technology provides real-time website safety ratings, warning users before visiting potentially dangerous sites. The software includes advanced ransomware protection with file backup and recovery capabilities.
Multi-Platform Support: McAfee Total Protection covers Windows, Mac, iOS, and Android devices under a single subscription, making it ideal for users with multiple devices.
Pricing: Annual subscriptions start around $44.99 for individual users, with family plans covering unlimited devices for approximately $84.99 per year.
Specialized Malware Removal Tools
1. ESET Online Scanner
ESET Online Scanner provides powerful one-time malware detection and removal without requiring software installation, making it perfect for emergency situations or second-opinion scanning.
Key Capabilities:
- Browser-based malware scanning
- Detection of rootkits and advanced threats
- Quarantine and removal of infected files
- Detailed scan reports with threat information
- No installation required for immediate use
This tool excels in situations where your primary antivirus may be compromised or when you need verification of potential infections. The online scanner uses ESET's award-winning detection technology without permanent system installation.
2. AdwCleaner by Malwarebytes
AdwCleaner specializes in removing adware, potentially unwanted programs, and browser hijackers that often slip past traditional antivirus software.
Specialized Features:
- Targeted adware and PUP removal
- Browser hijacker detection and cleanup
- Registry cleaning for malware remnants
- Toolbar and extension removal
- Reset browser settings to default
This lightweight tool focuses specifically on cleaning systems infected with advertising-related malware and unwanted software bundles commonly distributed through free software downloads.
3. HitmanPro
HitmanPro operates as a second-opinion scanner, using cloud-based detection engines from multiple security vendors to identify malware that single-vendor solutions might miss.
Advanced Detection Methods:
- Cloud-based multi-engine scanning
- Behavioral analysis for unknown threats
- Rootkit detection and removal
- Boot-time scanning capabilities
- Minimal system footprint during operation
HitmanPro excels at detecting sophisticated malware and advanced persistent threats through its multi-vendor approach and behavioral analysis capabilities.
4. Spybot Search & Destroy
Spybot specializes in detecting and removing spyware, adware, and other privacy-invasive software that may compromise personal information security.
Privacy Protection Features:
- Comprehensive spyware detection
- Privacy protection and tracking prevention
- Immunization against known malicious sites
- System file protection and monitoring
- Browser protection against malicious scripts
This tool focuses on protecting user privacy and preventing unauthorized data collection by malicious software and tracking systems.
Manual Malware Removal Techniques

Safe Mode Operations
Booting Windows in Safe Mode provides a controlled environment for malware removal by loading only essential system files and services. This prevents most malware from starting automatically and interfering with removal efforts.
Accessing Safe Mode: Restart your computer and press F8 repeatedly during startup (Windows 7) or hold Shift while clicking Restart (Windows 10/11). Select "Safe Mode with Networking" to maintain internet connectivity for downloading removal tools.
Safe Mode Benefits: Many malware programs cannot start in Safe Mode, making them easier to detect and remove. System resources are freed up for antivirus scanning, and network access allows for tool downloads and updates.
System Restore and Recovery
System Restore can help reverse malware damage by returning your computer to a previous state before infection occurred.
Using System Restore: Access System Restore through Control Panel > System and Security > System > System Protection. Choose a restore point dated before you noticed malware symptoms. Note that this may remove recently installed programs and updates.
Recovery Considerations: System Restore affects system files, installed programs, and registry settings but doesn't affect personal files. However, some advanced malware can infect restore points, making this method less effective against sophisticated threats.
Registry Cleaning and Repair
Malware often modifies Windows registry entries to maintain persistence and prevent removal. Careful registry cleaning can help eliminate malware remnants.
Registry Safety Precautions: Always create a registry backup before making changes. Use reputable registry cleaning tools rather than manual editing unless you have advanced technical knowledge. Incorrect registry modifications can render your system unbootable.
Common Malware Registry Locations:
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
Prevention Strategies and Best Practices
Layered Security Approach
Effective malware protection requires multiple security layers working together rather than relying on a single solution.
Essential Security Layers:
- Reputable antivirus software with real-time protection
- Firewall protection (Windows Firewall or third-party)
- Regular system and software updates
- Secure web browsing practices
- Email security and spam filtering
- Data backup and recovery planning
Security Software Combinations: Avoid running multiple real-time antivirus programs simultaneously, as they can conflict and reduce protection effectiveness. Instead, use a primary antivirus solution supplemented by on-demand scanners for additional verification.
Safe Computing Habits
Developing secure computing habits significantly reduces malware infection risks and complements technical security measures.
Email Security Practices: Never open email attachments from unknown senders or unexpected sources. Be cautious of emails with urgent language, spelling errors, or requests for personal information. Verify sender authenticity through alternative communication methods when suspicious.
Web Browsing Safety: Avoid clicking on suspicious links or advertisements, especially those promising prizes, warnings about infections, or too-good-to-be-true offers. Only download software from official websites or trusted sources. Use reputable browser extensions for additional security.
Software Installation Guidelines: Always download software from official sources rather than third-party download sites. Read installation prompts carefully to avoid bundled malware or unwanted programs. Keep software updated through official update mechanisms.
Regular System Maintenance
Consistent system maintenance helps prevent malware infections and ensures optimal computer performance.
Update Management: Enable automatic updates for Windows operating system and essential software. Regularly update antivirus definitions and security software. Install security patches promptly to address newly discovered vulnerabilities.
System Monitoring: Monitor system performance for unusual behavior or slowdowns. Check running processes regularly for unknown or suspicious programs. Review startup programs and disable unnecessary applications.
Backup Strategies: Implement regular data backup schedules using external drives or cloud storage. Test backup restoration procedures to ensure data integrity. Consider using automated backup solutions for consistent protection.
Comparing Free vs. Paid Solutions
Feature Comparison Analysis
Free antivirus solutions provide basic malware protection suitable for many users, while paid solutions offer comprehensive security suites with advanced features.
Free Solution Limitations:
- Limited customer support options
- Basic malware detection capabilities
- Minimal advanced threat protection
- No identity theft protection
- Limited or no VPN services
- Basic firewall protection
Paid Solution Advantages:
- 24/7 customer support availability
- Advanced threat detection technologies
- Comprehensive identity protection services
- Full-featured VPN services
- Enhanced firewall and network protection
- Additional privacy and security tools
Cost-Benefit Analysis
Evaluating the cost-effectiveness of security solutions involves considering both financial investment and potential data loss costs.
Hidden Costs of Free Solutions: While free antivirus software has no upfront cost, limitations may result in security gaps requiring additional tools or services. Time spent dealing with infections and system repairs represents hidden costs.
Value Proposition of Paid Solutions: Premium security suites often cost less than $100 annually while providing comprehensive protection that could prevent thousands of dollars in data loss, identity theft, or system replacement costs.
Performance Impact Considerations
Different security solutions have varying impacts on system performance, affecting daily computer usage and productivity.
Resource Usage Factors:
- Real-time scanning overhead
- Background update processes
- Memory and CPU utilization
- Disk space requirements
- Network bandwidth usage during updates
Optimization Strategies: Configure scans during low-usage periods, adjust real-time protection sensitivity based on usage patterns, and exclude trusted files and folders from scanning to improve performance.
Mobile and Cross-Platform Protection
Windows-Android Integration
Many users operate both Windows computers and Android devices, requiring coordinated security strategies across platforms.
Cross-Platform Threats: Malware can spread between devices through shared files, cloud storage, or network connections. Mobile malware may target data stored on computers or use mobile devices as attack vectors against computer networks.
Unified Security Solutions: Several security vendors offer multi-platform protection plans covering Windows, Android, iOS, and Mac devices under single subscriptions. This approach ensures consistent protection policies and centralized management.
Cloud Storage Security
Cloud storage services introduce additional security considerations requiring protection for data in transit and at rest.
Cloud Security Best Practices:
- Use strong, unique passwords for cloud accounts
- Enable two-factor authentication where available
- Encrypt sensitive files before cloud upload
- Regularly review cloud access permissions
- Monitor cloud account activity for unusual access
Integration with Security Software: Many premium security suites include cloud storage scanning capabilities, checking files for malware before synchronization and providing secure access to cloud services.
Troubleshooting Common Issues
False Positive Management
Security software occasionally identifies legitimate files as threats, requiring careful evaluation and management of false positive detections.
Identifying False Positives: Research flagged files through reputable sources, check file origins and digital signatures, and verify with multiple security tools when uncertain. Consider the file's behavior and purpose when evaluating threat reports.
Resolution Strategies: Add trusted files to antivirus exclusion lists, report false positives to security vendors for database updates, and maintain documentation of excluded files for future reference.
Performance Optimization
Security software can impact system performance, requiring optimization to balance protection effectiveness with usability.
Performance Tuning Options:
- Adjust scan schedules for off-peak hours
- Configure resource usage limits
- Optimize real-time protection settings
- Exclude trusted applications and folders
- Use cloud-based scanning when available
System Resource Management: Monitor CPU and memory usage during security scans, close unnecessary applications during full system scans, and consider upgrading hardware if security software consistently causes performance issues.
Infection Recovery Procedures
Complete malware removal may require multiple tools and techniques, especially for sophisticated infections.
Multi-Tool Approach: Use primary antivirus software for initial detection and removal, supplement with specialized removal tools for stubborn infections, and employ online scanners for verification and cleanup.
System Restoration Process: Document system state before and after removal attempts, use System Restore points when available, and consider clean operating system installation for severe infections that resist removal.
Future of Malware Protection
Emerging Threat Landscape
Cyber threats continue evolving, requiring adaptive security strategies and technologies to address new attack vectors.
AI-Powered Attacks: Artificial intelligence enables more sophisticated malware that can adapt behavior to evade detection, create personalized phishing campaigns, and automate large-scale attacks.
IoT and Connected Device Risks: Internet of Things devices create new attack surfaces and potential entry points for malware to access home and corporate networks.
Advanced Protection Technologies
Security vendors are developing new technologies to address evolving threats and improve protection effectiveness.
Machine Learning Integration: Advanced security solutions incorporate machine learning algorithms for behavioral analysis, predictive threat detection, and automated response capabilities.
Zero Trust Architecture: Zero trust security models assume no implicit trust and verify every access request, providing enhanced protection against advanced persistent threats and insider attacks.
Cloud-Based Protection: Cloud-based security services offer real-time threat intelligence, rapid update distribution, and collective defense capabilities across global user bases.
Conclusion
Protecting your Windows computer from malware requires a combination of reliable security software, safe computing practices, and regular system maintenance. Whether you choose free solutions like Malwarebytes, Windows Defender, or Avira, or invest in premium suites like Norton 360, Kaspersky, or McAfee, the key is selecting tools that match your security needs and usage patterns.
Remember that no single security solution provides perfect protection. Implementing layered security strategies, maintaining good computing habits, and staying informed about emerging threats creates the most effective defense against malware infections.
Regular system updates, cautious email and web browsing practices, and consistent data backup procedures complement your chosen security software to provide comprehensive protection. By combining the right tools with smart security practices, you can keep your Windows computer safe from malware while maintaining optimal performance and productivity.
The investment in quality malware protection, whether time spent configuring free tools or money spent on premium solutions, is minimal compared to the potential costs of system infections, data loss, or identity theft. Choose your security tools wisely, implement them properly, and maintain vigilant computing habits to ensure long-term protection for your digital life.
